OOPS! You forgot to upload swfobject.js ! You must upload this file for your form to work.
AMD Zen SEV protection found potential vulnerabilities
![]()
|
xtreview is your : Video card - cpu - memory - Hard drive - power supply unit source |
|
|||
|
|
||||
 Recommended : Free unlimited image hosting with image editor
Recommended : Free unlimited image hosting with image editor
|
POSTER: computer news || AMD ZEN SEV PROTECTION FOUND POTENTIAL VULNERABILITIES |
DATE:2016-12-10 |
|
|
In October, AMD has officially published the data on the built-in processor architecture Zen protection of virtual machines. Cloud services, as you might guess, are doing the work with remote services of a universal phenomenon and, therefore, become a stumbling block to malicious actions. AMD has decided to go at the head of the data protection process at the processor level and its cache. Thus, the server Zen version will have built-in Secure data encryption blocks Memory Encryption
(SME) and Secure Encrypted Virtualization (SEV). Documentation explaining how to work blocks are already in the public domain. Interestingly, based on the available data, two German security specialist could be found in the work of the mechanism of AMD Secure Encrypted Virtualization three potential vulnerabilities. a number of issues SEV technology recognized by them promising, but challenging. Looking ahead, we note that AMD has commented on the accusations in the shortcomings that Zen-generation products on the market yet, so can not speak about the vulnerability. S 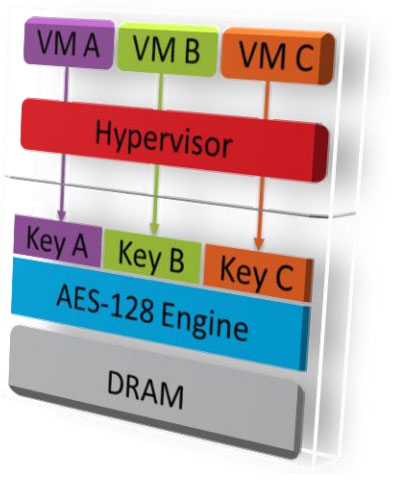 Before we talk about vulnerability, we recall that the SEV encrypts the data in the cache processor 128-bit AES-keys (with key for each virtual machine). The data is decrypted when loaded into the processor cache is encrypted and after unloading. Encryption and decryption work for memories and for applications. This allow to protect against attacks from a potentially vulnerable hypervisor. On paper it looks nice, but experts presented three scenarios, in which case the SEV protection may not work. Firstly, in the case of SEV does not provide encryption command control blocks, gave itself the hypervisor, which will bypass the SEV. Second, the values of the general-purpose registers in Zen is not encrypted, which leads to the potential leakage of critical data. Third, the realized investment management method such as nested page tables allow vulnerable hypervisor to control the virtual machine and apply the so-called replay attack (memory replay attacks). Once again I emphasize that all three scenarios exist only on paper, but what prevents implement them? Related Products : | ||
|
|
||
|
xtreview is your : Video card - cpu - memory - Hard drive - power supply unit source |
|
|
|
|
||
|
Xtreview Support  N-Post:xxxx Xtreview Support        |
AMD ZEN SEV PROTECTION FOUND POTENTIAL VULNERABILITIES |
| Please Feel Free to write any Comment; Thanks  |
The Japanese representation of AMD offered monetary compensation to the first buyers of Ryzen Threadripper (2017-09-08)
AMD itself would like to believe that mobile processors Ryzen have already been released (2017-09-08)
AMD gave details about the history of the Ryzen Threadripper (2017-09-06)
AMD processors with Zen architecture of the second generation will raise frequencies and specific performance (2017-09-05)
On the Germans, AMD Ryzen Threadripper processors produced a predominantly positive impression (2017-09-04)
More recent AMD Ryzen processors do not annoy Linux users with problems (2017-08-26)
Updated chipset drivers for AMD Ryzen and Ryzen Threadripper processors (2017-08-26)
We are looking at Noctua coolers for AMD Ryzen Threadripper (2017-08-25)
Japanese shops rushed to reduce prices for AMD processors Ryzen Threadripper (2017-08-24)
Ryzen Threadripper turned out to be so large that the waterblocks lack one sticker (2017-08-24)
RYZEN THREADRIPPER 1920X IHS OFF (2017-08-14)
kylake-X versus Ryzen Threadripper in extreme overclocking (2017-08-11)
instead of Ryzen Threadripper, buyers preferred motherboards (2017-08-11)
Details about the work of AMD Ryzen Threadripper with memory and PCIe peripherals (2017-08-11)
G.Skill Introduces Memory Kits for AMD Ryzen Threadripper Processors (2017-08-11)
Ryzen Threadripper number one (2017-08-07)
the first test results of AMD Ryzen Threadripper (2017-08-06)
German producers of water blocks prepare for the release of AMD Ryzen Threadripper (2017-08-05)
AMD Ryzen Threadripper 1920 will limit the value of TDP no more than 140 W (2017-08-04)
Japanese wait for night sales AMD Ryzen Threadripper (2017-08-04)
![]()
To figure out your best laptops .Welcome to XTreview.com. Here u can find a complete computer hardware guide and laptop rating .More than 500 reviews of modern PC to understand the basic architecture


7600gt review
7600gt is the middle card range.
We already benchmarked this video card and found that ...

 geforce 8800gtx and 8800gts
geforce 8800gtx and 8800gts  Xtreview software download Section
Xtreview software download Section  AMD TURION 64 X2 REVIEW
AMD TURION 64 X2 REVIEW  INTEL PENTIUM D 920 , INTEL PENTIUM D 930
INTEL PENTIUM D 920 , INTEL PENTIUM D 930  6800XT REVIEW
6800XT REVIEW  computer hardware REVIEW
computer hardware REVIEW  INTEL CONROE CORE DUO 2 REVIEW VS AMD AM2
INTEL CONROE CORE DUO 2 REVIEW VS AMD AM2  INTEL PENTIUM D 805 INTEL D805
INTEL PENTIUM D 805 INTEL D805  Free desktop wallpaper
Free desktop wallpaper  online fighting game
online fighting game  Xtreview price comparison center
Xtreview price comparison center Lastest 15 Reviews


Rss Feeds
Last News
- The new version of GPU-Z finally kills the belief in the miracle of Vega transformation
- The motherboard manufacturer confirms the characteristics of the processors Coffee Lake
- We are looking for copper coolers on NVIDIA Volta computing accelerators
- Unofficially about Intels plans to release 300-series chipset
- The Japanese representation of AMD offered monetary compensation to the first buyers of Ryzen Threadripper
- This year will not be released more than 45 million motherboards
- TSMC denies the presentation of charges from the antimonopoly authorities
- Radeon RX Vega 64 at frequencies 1802-1000 MHz updated the record GPUPI 1B
- AMD itself would like to believe that mobile processors Ryzen have already been released
- AMD Vega 20 will find application in accelerating computations
- Pre-orders for new iPhone start next week
- Radeon RX Vega 57, 58 and 59: the wonders of transformation
- ASML starts commercial delivery of EUV-scanners
- The older Skylake processors with a free multiplier are removed from production
- Meizu will release Android-smartphone based on Helio P40
- AMD Bristol Ridge processors are also available in American retail
- The fate of Toshiba Memory can be solved to the next environment
- duo GeForce GTX 1080 Ti in GPUPI 1B at frequencies of 2480-10320 MHz
- New Kentsfield overclocking record up to 5204 MHz
- Lenovo released Android-smartphone K8

HALO 3 HALO 3 - Final Fight!

PREY Prey is something you don t often see anymore: a totally unigue shooter experience.

computer news computer parts review Old Forum Downloads New Forum Login Join Articles terms Hardware blog Sitemap Get Freebies


